Earlier in March,Trend Micro published a research on a watering hole campaign targeting users in Southeast Asia with powerful spyware called LightSpy. Following that research,Kaspersky’sGlobal Research and Analysis Teamshared some importantadditional details on thisattack targeting mobile users through links on various forums and communications channels.
In their research, published on Securelist.com, Kaspersky provides analysis of:
• The surveillance framework’s deployment timeline starting from January 2020
• Previously unknown samples of the LightSpy Android implants
• Traces of implants targeting Windows, Mac and Linux based computers along with Linux-based routers
• New indicators of compromise and some other details about the attack
What is known about the LightSpy attacks?
Actors behind the campaigndistribute links to malicious websites mimicking the original ones that are likely to be frequented by potential victims. Once a target visits the weaponized website, a custom exploit chain tries to execute a shellcode, which leads to the deployment of the fully originalmalware on the victim’s phone
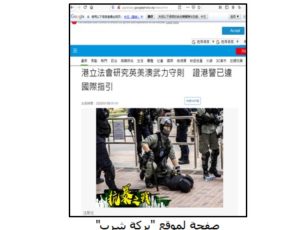
Landing page of watering hole site
The malware is successfully targeting iPhones running versions of iOS up to version12.2. Users running the latest version of iOS, 13.4, should be safe from these exploits.Users of
Android OS-based devices are also in the crosshairs – researchers found several versions of
the implant that target this platform.In addition, Kaspersky researchers identified some
indicators of the existence of malware targeting Mac, Linux andWindows-based computers,
along with Linux-based routers.
The research alsodiscovered the malware is being spread through forum posts and replies,
as well as popular communications platforms by posting links to the deployed landing pages. Once the website has been visited, the malware jailbreaks the victim’s device, giving
the attackers the ability to record calls and audio, read certain messengers and more.
The information currently availabledoes not make it possible to attribute the operation to
any known advanced persistence threat actor (APT), which is why Kaspersky has
temporarily dubbed the attackers “TwoSail Junk”.
“We tracked this particular framework and infrastructure beginning in January this year. It
is an interesting example of an agile approach to developing and deploying surveillance
framework in Southeast Asia. This innovative strategy is something we have seen before
from SpringDragon, and LightSpy’s targeting geolocation falls within the previous regional
targeting of the SpringDragon/LotusBlossom/Billbug APT, as does the infrastructure and
“evora” backdoor use. Although the campaign peaked in February – that is when we saw
the highest growth of links leading to the malicious site – it is still active and we continue
monitoring it,” comments Alexey Firsh, security researcher at Kaspersky’s Global Research
and Analysis Team.
 التكنولوجيا وأخبارها بوابة مصر لأخبار تكنولوجيا المعلومات والإتصالات وفي أفريقيا كما تعتبر مصدر رئيسي للمعلومات حول تكنولوجيا المعلومات والاتصالات والفرص الاستثمارية المرتبطة بالاقتصاد الرقمي في المنطقة بالكامل
التكنولوجيا وأخبارها بوابة مصر لأخبار تكنولوجيا المعلومات والإتصالات وفي أفريقيا كما تعتبر مصدر رئيسي للمعلومات حول تكنولوجيا المعلومات والاتصالات والفرص الاستثمارية المرتبطة بالاقتصاد الرقمي في المنطقة بالكامل







